As we increasingly rely on online platforms for our daily tasks for work, play, and entertaiment, the need for robust security measures cannot be overstated. One such measure is Two-Factor Authentication (2FA), a security protocol that adds an extra layer of protection to your online accounts and presence beyond a traditional username and password. This method ensures that online accounts remain secure, even if your password is compromised.
A commonly used form of 2FA is the Time-Based One-Time Password (TOTP). TOTP stands out for its effectiveness. This unique, temporary passcode, generated by an algorithm that uses the current time as a factor. It expires after a short period, rendering it useless to potential attackers even if intercepted.
One such platform is WordPress, a content management systems (CMS), which power countless websites, and are prime targets for cyberattacks. By incorporating 2FA and TOTP, WordPress not only secures its platform but also instills confidence in its users, making it more difficult for unauthorized access.
Understanding Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) is a security process that requires users to provide two distinct forms of identification before gaining access to an account or resources. It adds an extra layer of protection compared to just using a username and password. This process enhances security by combining three different factors:
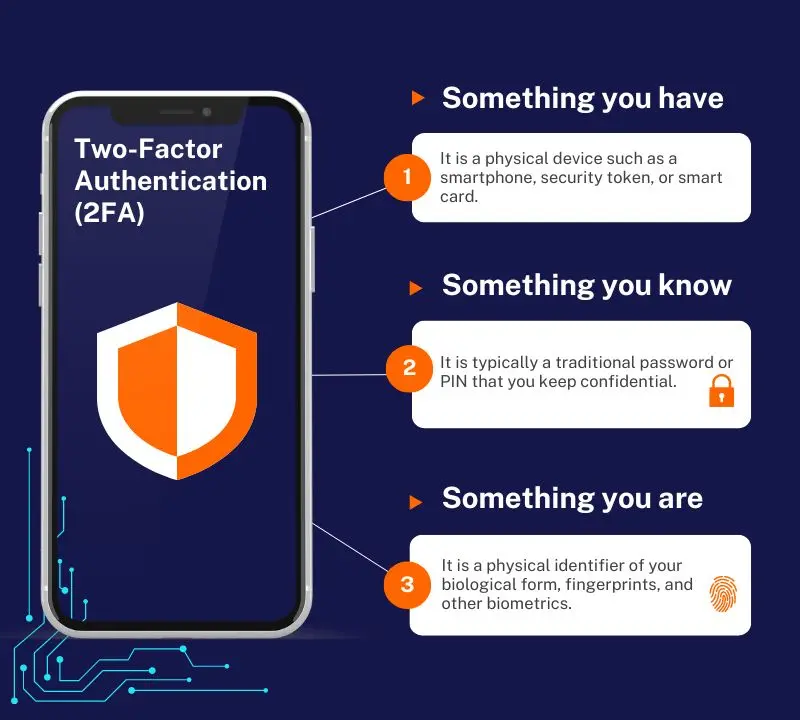
The idea behind 2FA is to create a layered defense that makes it more difficult for unauthorized persons to access an account or resources. If a password is compromised, the attacker still has at least one more barrier to breach before successfully breaking into. Implementing 2FA can protect against phishing, social engineering, and password brute-force attacks, and secures your logins from attackers exploiting weak or stolen credentials.
Time-Based One-Time Passwords (TOTP)
One of the most effective ways to safeguard your accounts and online resources is through 2FA, specifically using Time-Based One-Time Passwords (TOTP). TOTP is an essential component of modern security systems, providing an additional layer of authentication and protection beyond traditional passwords. It is a temporary and one-time passcode (OTPs), generated by an algorithm that uses the current time as a unique factor. It’s an extension of the HMAC-based One-Time Password (HOTP) algorithms, which is defined in RFC 4226. The key difference between TOTP and HOTP is HOTP generated passcodes based on a counter, TOTP generated passcodes based on the current time. TOTP codes are unique and only valid for a short period, typically 30 seconds. The time-based approach provides short-lived OTP values, which are desirable for enhanced security.
RFC 6238 TOTP: Time-Based One-Time Password Algorithm
The TOTP algorithm is defined in RFC 6238, the standard for Time-Based One-Time Password (TOTP). It provides a standardized approach to implementing TOTP, ensuring interoperability and security across different systems and applications that utilize time-based one-time password. The “Time-Based” approach with TOTP means even if an intruder manages to intercept the password, they won’t be able to use it after it expires.
The HOTP algorithm is based on HMAC-SHA1. The output is truncated to obtain user-friendly values. K and C represent the shared secret and counter value.
HOTP(K,C) = Truncate(HMAC-SHA-1(K,C))Mathematical formula for HMAC-SHA1 algorithm:
Hmac_K(M) = K_Pad xor inner_pad || H(K_Pad xor outer_pad || M)Since TOTP is an extension of HOTP, and it is a time-based variant, where value T (time step) replaces the counter C in HOTP. Its implementation may use HMAC-SHA-256 or HMAC-SHA-512 functions. And its value is calculated as follows:
TOTP = HOTP(K,T)T is an integer that signifies the count of time steps from the initial counter time, T0, to the present Unix time. For instance, consider that T0 is set to 0 and the Time Step X is 30. In this case, the value of T would be 1 if the current Unix time is 59 seconds. Similarly, T would be 2 if the current Unix is 60 seconds.
TOTP Validation Process
During a login attempt with 2FA and TOTP, the following validation steps occur:
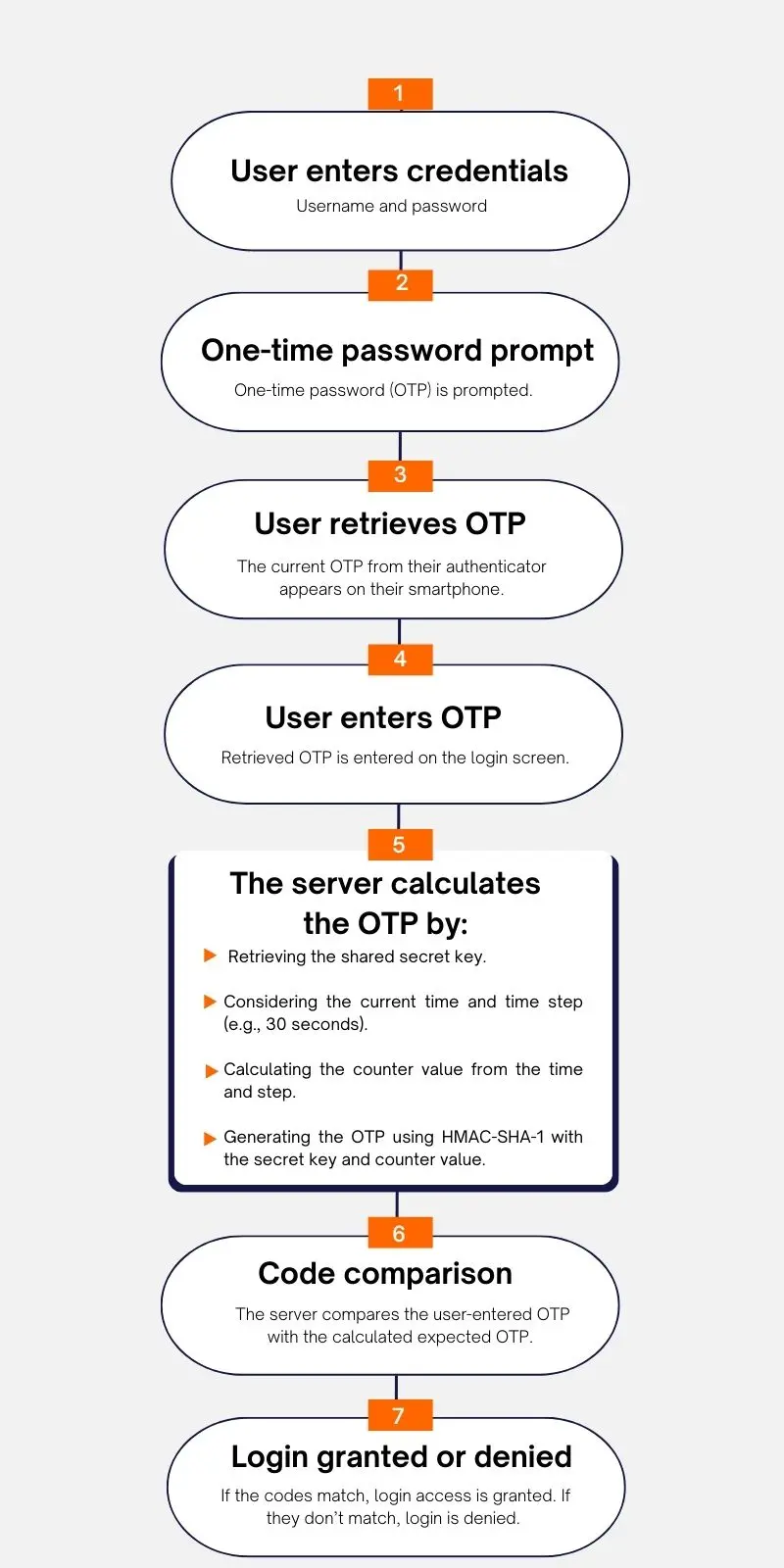
Time-Step Size in TOTP
The time step size is a crucial parameter in TOTP that defines how often the generated OTP changes. RFC 6238 recommends a default time step of 30 seconds. Here’s how time-step size affects the system:
TOTP Resynchronization
RFC 6238 acknowledges that user devices and servers might not have perfectly synchronized clocks, which could lead to failed login attempts even with a valid one-time password (OTP). To address this, the document recommends, but doesn’t mandate, a TOTP resynchronization mechanism.
The Clock Skew Challenge
TOTP Resynchronization Strategies
While not explicitly mandated by RFC 6238, some server implementations might employ resynchronization techniques to handle clock skews.
In today’s digital age, where data breaches and cyber attacks are increasingly common. TOTP stands out as a simple yet effective solution for enhancing security. Its ease of implementation and user-friendly nature make it a go-to choice for organizations looking to protect their users and customers. RFC 6238 standardizes this process, making TOTP a reliable and interoperable solution for 2FA in various online services, such as email, banking and other sensitive platforms such as WordPress. The short-lived one time OTP values are desirable for preventing replay attacks and unauthorized access, by providing a robust, standardized approach to two-factor authentication. Its adoption has led to a more secure and reliable method of verifying user identities across various digital platforms.
Furthermore, securing WordPress and apps goes beyond strong passwords. 2FA with TOTP offers a powerful solution. It offers an extra layer of defense. This extra layer makes it much harder for unauthorized access, and its seamless integration can enhance further protection.
Sources:
https://datatracker.ietf.org/doc/html/rfc6238
https://datatracker.ietf.org/doc/html/rfc4226