Understanding Brute-Force Attacks
Brute-force attacks are not only a nuisance but also pose a significant threat to the security, trust, and performance of WordPress websites. These attacks involve automated scripts or bots systematically attempting various username and password combinations until they gain access. The well-orchestrated attacks can strain server resources and compromise websites, where attackers install backdoors or malware to WordPress websites.
Attackers employ various techniques to identify vulnerabilities and initiate brute-force attacks. One common method involves obtaining a list of user accounts through endpoints such as the author-list page or exploiting vulnerabilities in WordPress plugins and endpoints.
Commonly Known Brute Force Attacks on WordPress
1. Author Enumeration:
curl -s -I -X GET https://yourwordpresssite.com/?author=1In a default WordPress installation, user IDs are assigned sequentially, starting with the administrator account typically having the ID of 1. If successful, the request often results in a redirect to a URL like
https://yourwordpresssite.com/author/username/, where ‘username’ is the actual username associated with the user ID 1.
This revelation of the ‘username’ is significant because it provides potential attackers with valuable information that can be exploited in brute force attacks. By knowing a valid username, attackers can streamline their efforts to guess passwords associated with that username. Since usernames are often used as part of the login credentials, this information significantly reduces the complexity of brute force attacks, making them more likely to succeed.
2. REST API User Endpoint:
http://yourwordpresssite.com/wp-json/wp/v2/users The /wp-json/wp/v2/users endpoint, part of the WordPress REST API, which is also accessible through the query parameters format, using ?rest_route=/wp/v2/users, enables developers to remotely interact with WordPress sites by exchanging JSON data.
https://yourwordpresssite.com/?rest_route=/wp/v2/users This endpoint serves as a gateway to user-related information, encompassing user profiles and details of registered users within the WordPress site. Both methods are interchangeable, leading to the same endpoint and producing identical responses. This flexibility enhances developers’ ability to access user data programmatically, facilitating seamless integration with external applications and services.
Alongside the user endpoint, other key endpoints like
https://yourwordpresssite.com/wp-json/wp/v2/postshttps://yourwordpresssite.com/wp-json/wp/v2/commentscan be used to list all posts and comments on the site. Additionally, the oEmbed endpoint,
https://yourwordpresssite.com/wp-json/oembed/1.0/embed?url=POST-URL, offers metadata about posts, including author information and timestamps, which is invaluable for building engaging user experiences. While these endpoints don’t inherently expose user information, they provide rich metadata about user activity, enhancing developers’ ability to craft personalized and immersive digital experiences.
However, this reliance on the REST API necessitates stringent security measures, as attackers can exploit exposed endpoints to gather intelligence and launch targeted attacks, underscoring the importance of robust authentication, authorization, and access control mechanisms. Despite these challenges, the WordPress REST API remains a cornerstone of headless WordPress architectures, empowering developers to create flexible, scalable, and feature-rich web applications.
3. XML-RPC Endpoint:
curl -X POST \
-H 'Content-Type: text/xml' \
-d @request.xml \
http://yourwordpresssite.com/xmlrpc.php
The XML-RPC (Remote Procedure Call) endpoint allows remote procedure calls to WordPress, including functions for managing posts, users, and other site features. It facilitates various functionalities, such as publishing content, managing comments, and authenticating users remotely.
The xmlrpc.php file can be exploited by attackers to execute brute-force attacks against WordPress login credentials. Since XML-RPC allows remote authentication and login attempts, attackers can abuse this functionality to guess usernames and passwords programmatically.
Attackers send POST requests to the xmlrpc.php file, attempting to authenticate using different username and password combinations [1].
Using automated scripts or open-source tools like Burp Suite or Metasploit, attackers can systematically try various username and password combinations until they successfully authenticate and gain unauthorized access to a WordPress site.
It’s worth noting that while WPScan is an invaluable publicly available tool for security professionals to gather information and identify potential vulnerabilities on WordPress sites, it also means that attackers can use it to exploit your site. WPScan can enumerate usernames, detect installed plugins and themes, and find security issues, providing attackers with crucial information to target specific vulnerabilities. Therefore, blocking automated tools from accessing your WordPress endpoints is essential to prevent unauthorized access and potential exploitation. One possible solution is to hide your WordPress site completely from WPScan, which will be a future blog topic.
Securing These Endpoints
While you can use server-level configurations, such as Apache (.htaccess) or Nginx (server block), to block these endpoints that expose user information or facilitate brute-force attacks, you can also leverage Cloudflare Web Application Firewalls (WAFs) to block malicious traffic and unauthorized access attempts. Cloudflare WAFs provide an additional layer of security by filtering and monitoring HTTP requests to identify and block threats before they reach your server.
Another important aspect of blocking access to xmlrpc.php in WordPress is not only help preventing brute-force and ping-back attacks but it subsequently mitigates the risk of amplification attacks, potentially leading to Distributed Denial of Service (DDoS) incidents if left unaddressed.
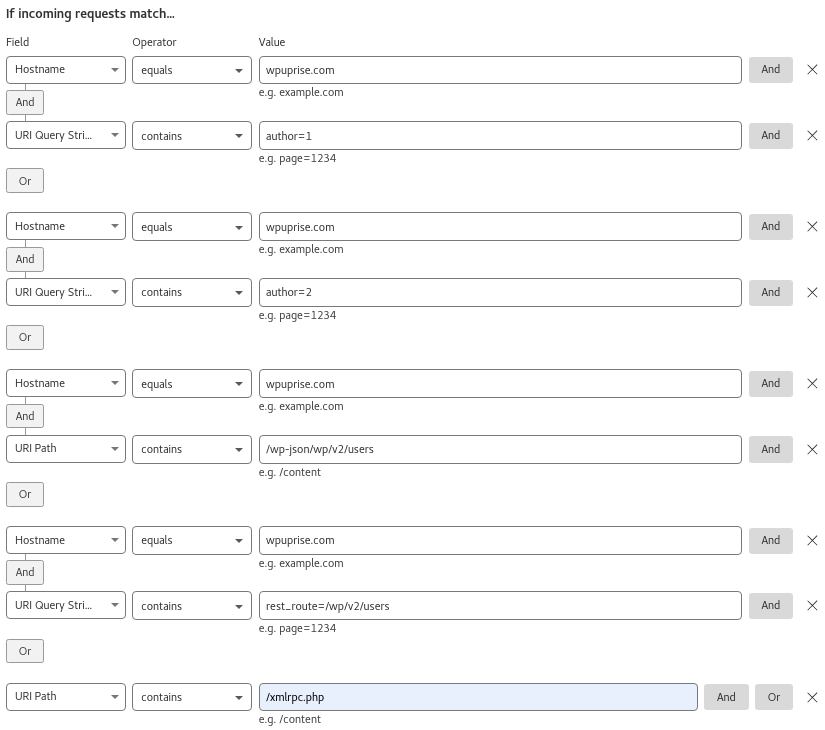
Expression Preview
(http.host eq "wpuprise.com" and http.request.uri.query contains "author=1")
or (http.host eq "wpuprise.com" and http.request.uri.query contains "author=2")
or (http.host eq "wpuprise.com" and http.request.uri.path contains "/wp-json/wp/v2/users")
or (http.host eq "wpuprise.com" and http.request.uri.query contains "rest_route=/wp/v2/users")
or (http.request.uri.path contains "/xmlrpc.php")
Then take action…
BlockWe Are Not Done Here
With an army of bots and attackers preying on WordPress and other known CMS platforms like Drupal and Joomla safeguarding your site should be taken seriously to protect it from these constant threats. Blocking or restricting access to the wp-admin URL can significantly enhance your site’s security by preventing unauthorized access attempts.
Simply changing the URL for wp-admin is not a comprehensive security measure because attackers can potentially discover the new URL through various scanning techniques. To effectively secure your WordPress admin area, a layered security approach combining multiple strategies is needed.
Here are some strategies you can implement:
1. Two-Factor Authentication (2FA)
Implementing 2FA adds an additional layer of security. Even if an attacker discovers the wp-admin URL, they would still need a second form of authentication to gain access.
2. Fail2Ban
Fail2Ban is a software that monitors log files and bans IP addresses that show malicious signs, such as too many password failures. It can help mitigate brute force attacks by banning IPs after a certain number of failed login attempts.
On Cloudflare, you could use:
1. Cloudflare Access
Cloudflare Access allows you to protect the wp-admin area by requiring users to authenticate via Cloudflare before they can even reach your server. This can include enforcing 2FA, single sign-on (SSO), and other identity verification methods.
2. Cloudflare Rate Limiting
Implementing rate limiting rules in Cloudflare can help mitigate brute force and DDoS attacks. By limiting the number of requests a user can make to the wp-admin URL, you can reduce the likelihood of successful attacks.
3. Cloudflare WAF Rules
Limiting access to your wp-admin area based on IP address, ASN, or geolocation can significantly reduce the attack surface.
1. Geolocation: Geolocation restrictions can help block access from certain countries or regions, but they are not foolproof. Users can easily bypass these restrictions by using VPNs or proxies that make it appear as though they are accessing the site from a different location. Therefore, while geolocation can be a useful layer of security, it should not be relied upon as the sole method of protection.
2. IP whitelisting: Allowing only authorized IPs to access the administrative dashboard provides complete control over access permissions, significantly reducing the risk of unauthorized login attempts, but it may be inconvenient to keep up with authorized users’ constantly changing IP addresses, especially if you have a large user base needing access to the admin page.
One way to find a workaround is to identify the IP subnet range of your users’ ISPs and add these ranges to a Cloudflare List. Cloudflare Lists enable you to group IP addresses, IP ranges, or other values into a reusable set that can be applied across different firewall rules.
This approach can simplify the management of access controls by allowing you to update a single list instead of multiple individual IP addresses. Each list can contain up to 10,000 entries, making it a scalable solution for managing a large number of authorized IP ranges.
3. ASN: Restricting access using ASN (Autonomous System Number) can be an effective method for controlling who can access your WordPress administrative dashboard. ASNs are used by Internet Service Providers (ISPs), large enterprises, and other organizations that manage their own networks and route their own traffic. Each ASN is assigned by a regional internet registry (RIR) and is unique, allowing different networks to be identified and managed independently on the global internet.
To find the ASN of your Internet Service Provider, you first need to identify your current IP address. You can easily do this by typing ‘what is my IP address’ into Google. Once you have your IP address, you can use a whois tool or command to find the corresponding ASN.
When you have the list of geo locations, ASNs, and IP address information ready, you can create WAF (Web Application Firewall) rules to restrict your site’s administrative areas.
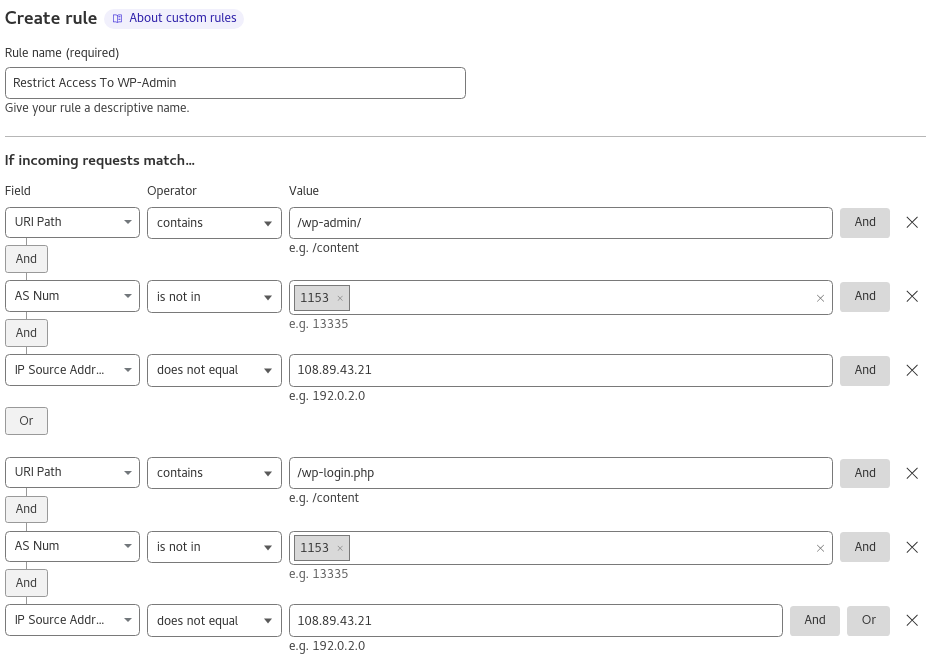
Expression Preview
(http.request.uri.path contains "/wp-admin/" and not ip.geoip.asnum in {1153} and ip.src ne
108.89.43.21) or (http.request.uri.path contains "/wp-login.php" and not ip.geoip.asnum in {1153} and ip.src ne 108.89.43.21)
Then take action…
Block
Conclusion
Protecting your WordPress website against brute-force password guessing attacks requires proactive measures and robust security protocols. By blocking author enumeration, XML-RPC, and REST API user endpoints, and combining this with access restrictions to /wp-admin URL based on specific criteria such as IP address, Autonomous System Number (ASN), or geolocation, you can fortify your website’s defenses and safeguard sensitive information from malicious actors. Remember, prioritizing strong password practices, keeping your themes and plugins up-to-date, and staying vigilant against emerging threats are essential aspects of maintaining a secure online presence.
Source: https://ieeexplore.ieee.org/abstract/document/9519384