Despite the rise of messaging services and other forms of communication such as video calls and collaboration tools, email continues to be the primary channel for business communication. One of the most effective ways to ensure the confidentiality, integrity, and authenticity of your emails is through S/MIME (Secure/Multipurpose Internet Mail Extensions). S/MIME is the protocol for email encryption and digital signatures. It requires both the sender and recipient to have S/MIME certificates installed. However, managing S/MIME certificates can be complex and time-consuming. That’s where S/MIME certificate management solutions come in. It simplifies the process and ensures seamless email security for everyone.
To simplify and streamline the process of S/MIME digital certificate, RFC 8823 standard was developed. It is based on and an extension of AMCE RFC 8555, to support the issuance and management of S/MIME certificates. While RFC 8555 primarily focuses on domain validation certificates for securing web HTTPS, RFC 8823 adapts and extends these mechanisms to handle the unique requirements of S/MIME.
Email remains a critical communication channel for businesses and individuals. But it’s also a prime target for cyber threats, including phishing and spam, malware, and unauthorized access.
1. Preventing Cyber Attacks
Email is a common way for various cyberattacks, such as phishing, business email compromise, and malware distribution. Effective email security solutions help identify and block these threats.
2. Protecting Sensitive Data
Emails often carry confidential information. Robust email security measures like encryption and strong authentication mechanisms prevent unauthorized access. Likewise, compliance requirements mandate the protection of personal and sensitive data. Non-compliance can result in severe penalties and reputational damage.
3. Maintaining Privacy
Email security ensures that your private communications remain confidential. Encryption prevents unauthorized individuals from reading your emails, protecting your personal information from prying eyes.
4. Mitigating Social Engineering Threats
Email security measures help prevent spoofing and impersonation attacks, where attackers disguise themselves as legitimate entities to deceive recipients. Furthermore, training users to identify phishing scams and avoid suspicious links bolsters overall email security.
Encryption is a fundamental component of email security. By encrypting emails, you ensure that only intended recipients can read the message content, preventing unauthorized access. S/MIME encryption adds a layer of security by using public key infrastructure (PKI) to encrypt and decrypt messages. This encryption method ensures that even if emails are intercepted, they remain unreadable without the appropriate decryption key.
End-user S/MIME refers to the use of S/MIME (Secure/Multipurpose Internet Mail Extensions) technology for securing email communications by individual users. In essence, end-user S/MIME empowers individuals to:
Encrypt Emails:
Users can send encrypted emails that can only be decrypted and read by the intended recipient. This protects sensitive information from unauthorized access, ensuring privacy and confidentiality.
Digitally Sign Emails:
Users can add a digital signature to their emails, providing proof of their identity as the sender. This assures the recipient that the message has not been altered or tampered with during transit.
An end-user S/MIME certificate includes a public key for encrypting emails and a private key for decrypting received messages and applying digital signatures. These certificates are typically issued by a Certificate Authority (CA) and help establish trust in email communications.
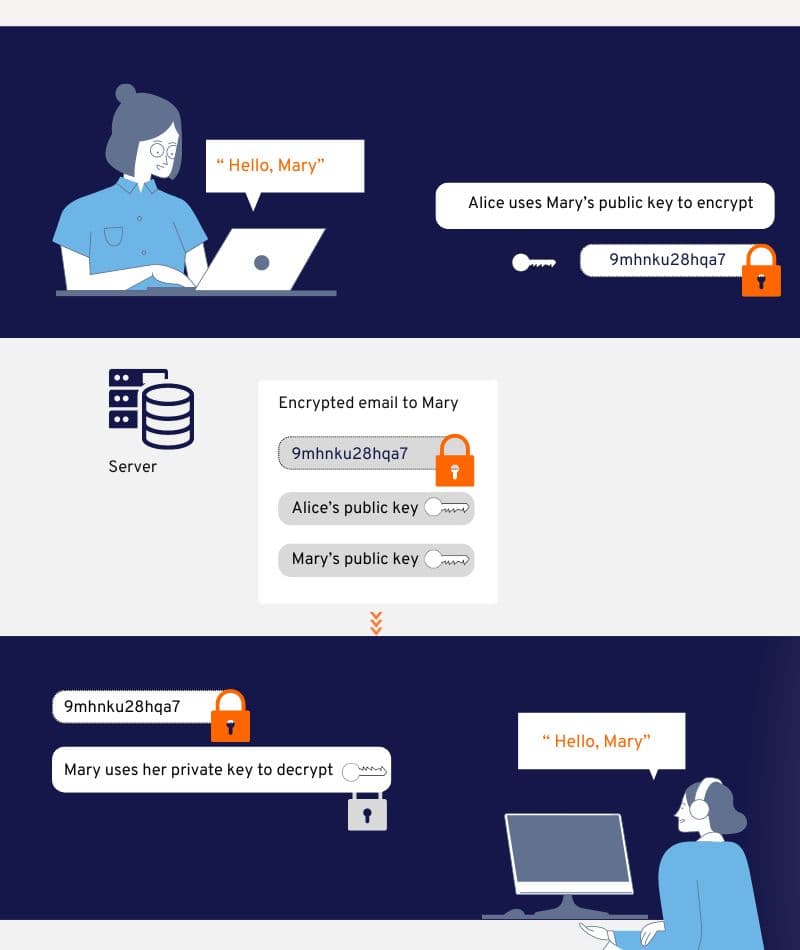
1. Public Key Encryption
Alice’s Side: When Alice wants to send an encrypted email to Mary, she needs Mary’s public key to encrypt the message. This public key is part of Mary’s S/MIME certificate, which Alice must have previously obtained.
2. Encryption Process
Alice Encrypts: Alice’s email client uses Mary’s public key to encrypt the message. This ensures that only Mary can decrypt the message, as only Mary has the corresponding private key.
3. Transmission
Email Server: The encrypted email is sent to an email server. The email server transmits this encrypted message to Mary. During this transmission, the message remains encrypted and secure.
4. Decryption Process
Mary’s Side: When Mary receives the email, her email client uses her private key to decrypt the message. This private key is securely stored on her device and is not shared with anyone else.
5. Viewing the Message
Mary Reads: Once decrypted, Mary can read the email content. The email client performs the decryption locally, ensuring the message’s confidentiality.
Implementing S/MIME (Secure/Multipurpose Internet Mail Extensions) for end-users offers significant security benefits, but it also presents several challenges. Users need to manage their own certificates, including renewal and revocation, which can be cumbersome for non-technical users. End-users often need training to understand how to use S/MIME effectively, including how to sign, encrypt, and verify emails. This training can be time-consuming and may require ongoing support.
S/MIME certificates have a finite lifespan and must be renewed periodically. Managing these renewals can be cumbersome, especially if users forget to renew their certificates, leading to disruptions in email security. If a certificate is compromised or needs to be revoked, the process must be seamless and quick to avoid security risks.
RFC 8823 protocol, an extension of RFC 8555, has revolutionized S/MIME certificate management by introducing automation and standardization through the ACME (Automatic Certificate Management Environment), specifically for end-user S/MIME certificates. While RFC 8555 is using “dns” identifier type, RFC 8823 introduces a new identifier type called “email”, enabling it to handle email addresses for S/MIME certificates.
RFC 8823 adds new challenges tailored for email address validation:
RFC 8823 leverages the existing ACME infrastructure. It reuses much of the existing ACME protocol framework defined in RFC 8555. This allows CAs and clients to leverage their existing ACME infrastructure to support S/MIME certificates with minimal changes. This reduces the need for developing separate systems and streamlines the adoption of S/MIME. Thus, it enables the automation of S/MIME certificate issuance and management, making it easier and more accessible for end-users to secure their email communications.
In an era where email remains a cornerstone of communication, securing email is a necessity. The implementation of robust email security measures, such as encryption and digital signatures, ensures that sensitive information remains confidential. S/MIME certificate management offers a powerful solution, combining robust encryption with streamlined automation to protect your sensitive information, ensure regulatory compliance, and bolster overall cybersecurity.
RFC 8823, extending the ACME protocol defined in RFC 8555, streamlines the process of issuing and managing S/MIME certificates, making it easier for organizations to enhance their email security and maintain compliance. The introduction of email-based challenges ensures that certificates are issued only to legitimate email owners, bolstering the integrity of S/MIME and enhancing overall email security.
Sources:
https://datatracker.ietf.org/doc/rfc8823/
https://datatracker.ietf.org/doc/rfc8555/