Have you ever noticed that little padlock icon (Safari, Edge) or little tune icon (Chrome) in your browser’s address bar when you visit certain websites? That tiny symbol represents a massive effort to keep your online interactions private and secure. The technologies behind it are SSL (Secure Sockets Layer), TLS (Transport Layer Security), HTTPS (Hypertext Transfer Protocol Secure).
Whether you’re shopping online, logging into your bank account, or simply browsing the web, SSL/TLS and HTTPS are essential for protecting your sensitive information from hackers and cybercriminals. These technologies also help verify the authenticity of websites, ensuring you’re not connecting to a malicious imposter.
By understanding these fundamental technologies, you’ll be equipped to ensure the privacy and security of user data, build trust, and comply with industry standards. Furthermore, for WordPress, WooCommerce and other applications, SSL, TLS and HTTPS are not just optional – they’re fundamental and a requirement. Understanding them is key to building a successful and secure digital platform, and enhances your brand reputation and fosters long-term success.
SSL stands for Secure Socket Layer. It is a protocol that creates an encrypted connection between your browser and the website you’re visiting. This encryption scrambles your data, making it gibberish to anyone who tries to intercept it. Though the SSL protocol has been succeeded and deprecated by TLS (Transport Layer Security), the terms SSL and SSL/TLS digital certificate are often used interchangeably. The fundamental concepts and principles introduced by SSL formed the basis for TLS, which continues to evolve and improve upon the foundation laid by its predecessor.
TLS stands for Transport Layer Security, and it’s often called an SSL or SSL/TLS digital certificate. By building upon the foundation of SSL and addressing its weaknesses, TLS has become the de facto standard for secure communication on the Internet, ensuring its connection remains private and integral.
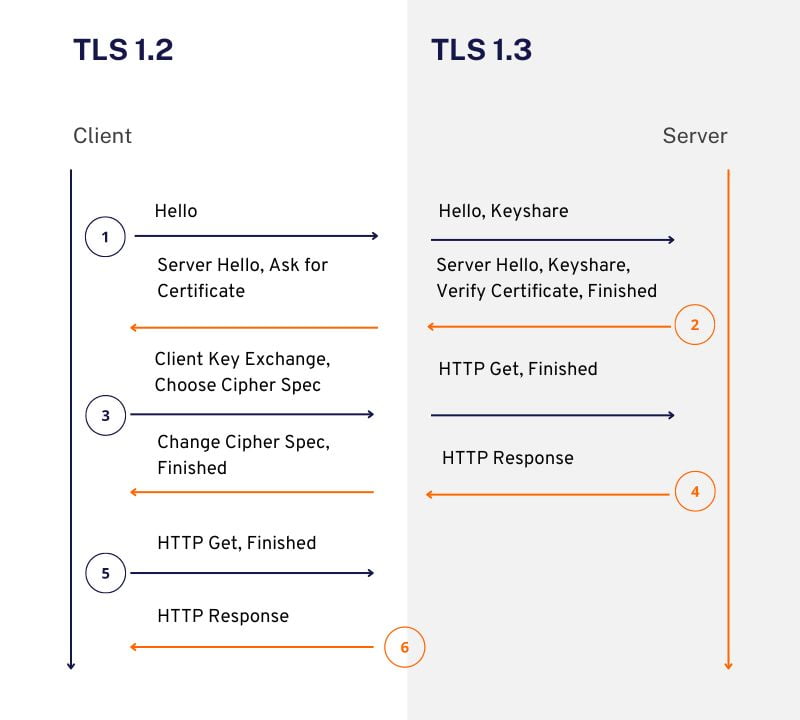
With the latest version, TLS 1.3, marks a significant leap forward in securing internet communications. As the newest iteration of the TLS protocol, it builds upon the previous iteration (TLS 1.2) to offer enhanced security, improved performance, and heightened privacy. It is constantly evolving, with new versions and protocols being developed to address emerging security threats.
TLS uses a combination of symmetric and asymmetric cryptography for optimal security and performance. Likewise, digital certificates play a crucial role in establishing trust and security between the client (web browser) and server (website). It provides authenticity, encryption and trust between the 2 parties that the messages have not been altered in transit. Finally, public key infrastructure (PKI) provides the underlying trust infrastructure for TLS. It ensures that the server is who it claims to be, protects the confidentiality and integrity of data transmitted between browser and websites.
A combination of both symmetric and asymmetric encryption is a great way for TLS. Asymmetric encryption is used for the initial handshake and key exchange, while symmetric encryption handles the bulk of data encryption for faster performance.
TLS handshake protocol redefines how secure connections are established between your web browser and a website. It is a series of steps taken before any data is exchanged, ensuring both parties can trust each other and agree on how to encrypt information.
TLS 1.3, built upon TLS 1.2, introduces several key features that significantly improve the security, performance, and privacy of online communication. One major enhancement is 0-RTT (Zero Round Trip Time) resumption, which allows for faster connection establishment by resuming sessions without a full handshake in certain scenarios. Additionally, TLS 1.3 mandates the use of modern, more secure ciphers and key exchange mechanisms, strengthening protection against known vulnerabilities. The fundamental behind TLS encryption known as the “handshake” process is streamlined, reducing complexity and potential errors.
HTTPS is the secure version of the standard web protocol. It leverages SSL/TLS to encrypt the communication between a web browser and a website. This encryption ensures that the data exchanged between them remain confidential and cannot be easily intercepted or tampered with by malicious actors. By adding this layer of security, using the SSL/TLS handshake standard, HTTPS protects sensitive information like passwords, credit card numbers, and personal details, while also providing authentication and data integrity. Today, HTTPS is widely adopted as the standard for secure web communication, and most browsers warn or block users from accessing sites that are unencrypted.
SSL, the precursor, laid the groundwork with its encryption and authentication concepts. TLS, its evolved successor, fortified these foundations, addressing vulnerabilities and enhancing overall security. his encryption acts like an unbreakable code, scrambling your information so that only the intended recipient can decipher it. Together, they form the cryptographic engine that powers HTTPS, the secure version of the web protocol we use daily.
When you visit a website starting with “https://” and see that reassuring padlock/tune icon, you can confidently browse, shop, and interact online, knowing that your data is protected. Your sensitive information is encrypted and safeguarded. But it’s not just about privacy; it’s about trust. HTTPS verifies the identity of websites, ensuring you’re interacting with the legitimate entity, not a malicious imposter.
For WordPress websites and WooCommerce stores, SSL/TLS encryption is not just a technicality; it’s a business imperative. By encrypting sensitive data like login credentials and payment information, SSL/TLS protects both customers and merchants from fraud and data breaches. It safeguards user data in transit, protecting against eavesdropping and tampering, and ultimately providing a secure and seamless user experience.
Sources:
https://datatracker.ietf.org/doc/html/rfc8448/
https://datatracker.ietf.org/doc/html/rfc8446
https://datatracker.ietf.org/doc/html/rfc5246
https://datatracker.ietf.org/doc/html/rfc6101
https://datatracker.ietf.org/doc/html/rfc7230